WordPress is the most popular CMS on the internet. There are over 74 MILLION sites running on WordPress. Running a website on such a popular platform also means that it’s one of the most highly targeted platforms by hackers. However, while WordPress’ code base is rock solid and is continuously developed to ensure that it stays as secure as possible, there is always the possibility of good ol’ human error that can come into play, making a WordPress site easy prey for those pesky hackers.
Here at Uptown Studios, we host and manage close to 130 sites running on WordPress, so ensuring they are all in tip-top shape in the security department is one of my top priorities. To stay on top of it all, I have put together 10 Point Strategy to Beef Up Security on your WordPress Site.
1. Limit Login Attempts
Install some sort of login attempts plugin. There is a really simple one called Limit Login Attempts that works great. It says its really old in the WP plugin repository, but everywhere I read about this plugin says that for the purpose it serves, it does not matter that it’s so old. There is also Jetpack’s Protect option. It comes bundled with Jetpack, a plugin by Automattic. Or there is Wordfence Security. I can’t recommend WordFence enough. It’s great.
2. Secure Critical WordPress Directories Using .htaccess
I also lock down attempts to open and edit files inside wp-includes and the wp-config.php file by adding a few lines to my .htaccess file. Add this to the top of the .htaccess file:
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteBase /
RewriteRule ^wp-admin/includes/ – [F,L]
RewriteRule !^wp-includes/ – [S=3]
RewriteRule ^wp-includes/[^/]+.php$ – [F,L]
RewriteRule ^wp-includes/js/tinymce/langs/
RewriteRule ^wp-includes/theme-compat/ – [F,L]
</IfModule>
<files wp-config.php>
order allow,deny
deny from all
</files>
3. Lock Down PHP File Execution Inside the Uploads Folder
Also, create another .htaccess file inside the uploads folder. Since this folder has to have 777 permissions on most servers, hackers will exploit this and add PHP files to do malicious deeds to the various folders inside the uploads folder. To prevent PHP file execution inside the Uploads directory, create the file inside wp-content/uploads and add this to it:
Order Deny,Allow
Deny from All
</Files>
4. Disable the Built in File Editor
For the life of me I can’t understand why WordPress still allows file editing from within the WP admin console. If you hover over Appearance you will see ‘Editor’ and also in Plugins you will see ‘Editor.’ While this may be super convenient for some, this is a HUGE security hole. Unless you are limiting login attempts, a hacker or spam bot can bash their way in to your WordPress admin area and then have their way with all of the template and plugin files. To disable the editor, open the wp-config.php file in your favorite text editor application and then add the following line to the bottom of the document just before the /* That’s all, stop editing! Happy blogging. */ line:
And voila!
5. Change Ownership of All Files to a Specific FTP User
Another way to harden the site is, if you have access to Linux Command Line for your server, to change ownership for all files in a specific vhost (or domain) to a single user that is not the root user on the server. You can do this by first creating this new user, then cd-ing into the directory above your all of a domain’s website files and running a command in the command line. Here is an example of how it looks on our server:
[root@cloud-sever-01 vhosts]# chown -R username:groupname *
The directory tree could be different for your server, but the chown command would be the same. The document root folder and vhost folder would still need to be owned by either the root user or apache, but all of the files inside the document should be owned by a user with far less privileges on the server. That way, if the user is ever compromised only that specific vhost is subject to being subverted, not the entire sever.
6. Set the Permissions for Files and Folders
You also want to make sure all files and folders in your WordPress install have been set with the proper permissions. Files should have permissions set to 644 and folders to 755, with the exception being the uploads folder and all of its child folders.
7. Remove the ‘admin’ User
When installing WordPress, the default username that most people set up as their administrator account is simply called ‘admin’. If your installs have a user called admin, delete it! That is the first thing hackers will attempt when bashing into your site. You can do this by first creating a new user in WordPress. Call it something random. Don’t use the website name or company name or any other commonly used names (such as webmaster, administrator, or webadmin). Give this user an Administrator role – then, log out and log back in using this new user. Go to Users again and delete the old admin user. When asked what to do with its posts, attribute them to the new Administrator you just created. Once that is done, go back into the new users settings and give it a nickname of something that is neither the website name, company name, nor username. Sometimes the nickname can be a give away to hackers as to what the username is.
8. Don’t Use ‘wp_’ Database Table Prefixes
Another thing you should do is change the database table prefix. This is always one of the first things I do when setting up a new WordPress site. If you are creating a brand new WordPress site, you can make this edit inside the wp-config.php file prior to installing WordPress on the server for the first time. To do this, open wp-config.php and edit the line that looks like this:
And make it look something like this:
When hackers attempt to inject malicious SQL code into your database, knowing what the table prefixes are is a like giving them a helping hand in messing your site up. By assigning a random value to your database prefixes, you can make a hackers life much harder and your life much easier.
If you have a pre-existing WordPress site, then this kind of thing can be a bit tricky. Be sure you backup all of your database tables before attempting this and then check out this article for how to change your database table prefixes: http://www.wpbeginner.
9. Always Use a Secure Password or Pass Phrase
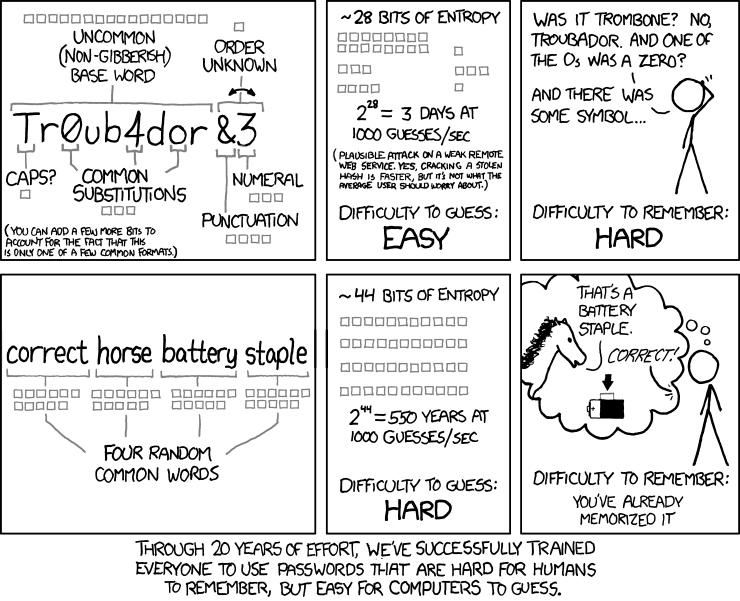
Hackers are quite good at guessing passwords. Hackers have programs that can make thousands of guesses per second, so even the most secure passwords of 12 to 16 characters (consisting of letters, numbers and symbols) can be cracked in only a matter of days. By using secure Pass Phrases (such as ‘river dancing creeps me out’) as opposed to Passwords we can turn that 3-day turnaround into about a half a millennium turnaround. Check out this classic xkcd comic strip explaining how this works:
10. Keep WordPress Plugins and Core Up To Date
The last recommendation I have for you is to always stay up to date on plugins and especially the WordPress core. The greatest strength WordPress has is its community. They are constantly finding new holes and exploits and as a result, the WordPress team churns out security updates all the time. Lately it has been pretty frequent (something like 12 this year) but usually there are about 3 to 4 times per year. The way they get reported is usually in a quite responsible manner so hackers only learn about them once WordPress releases the update and tells people about it. So update as soon as possible to keep things secure.
So there you have it – our top 10 tips for securing your WordPress site. The above should definitely be a huge help to hardening your WordPress installs. If you need any help or have additional questions, give Uptown Studios a call at (916) 446-1082 or email us at tina@uptownstudios.net.